Data Centre Security
Effectively Secure Your Virtual, Cloud, Physical,
and Hybrid Data Environments.
The Greatest Asset to
Any Business is a Client’s Trust
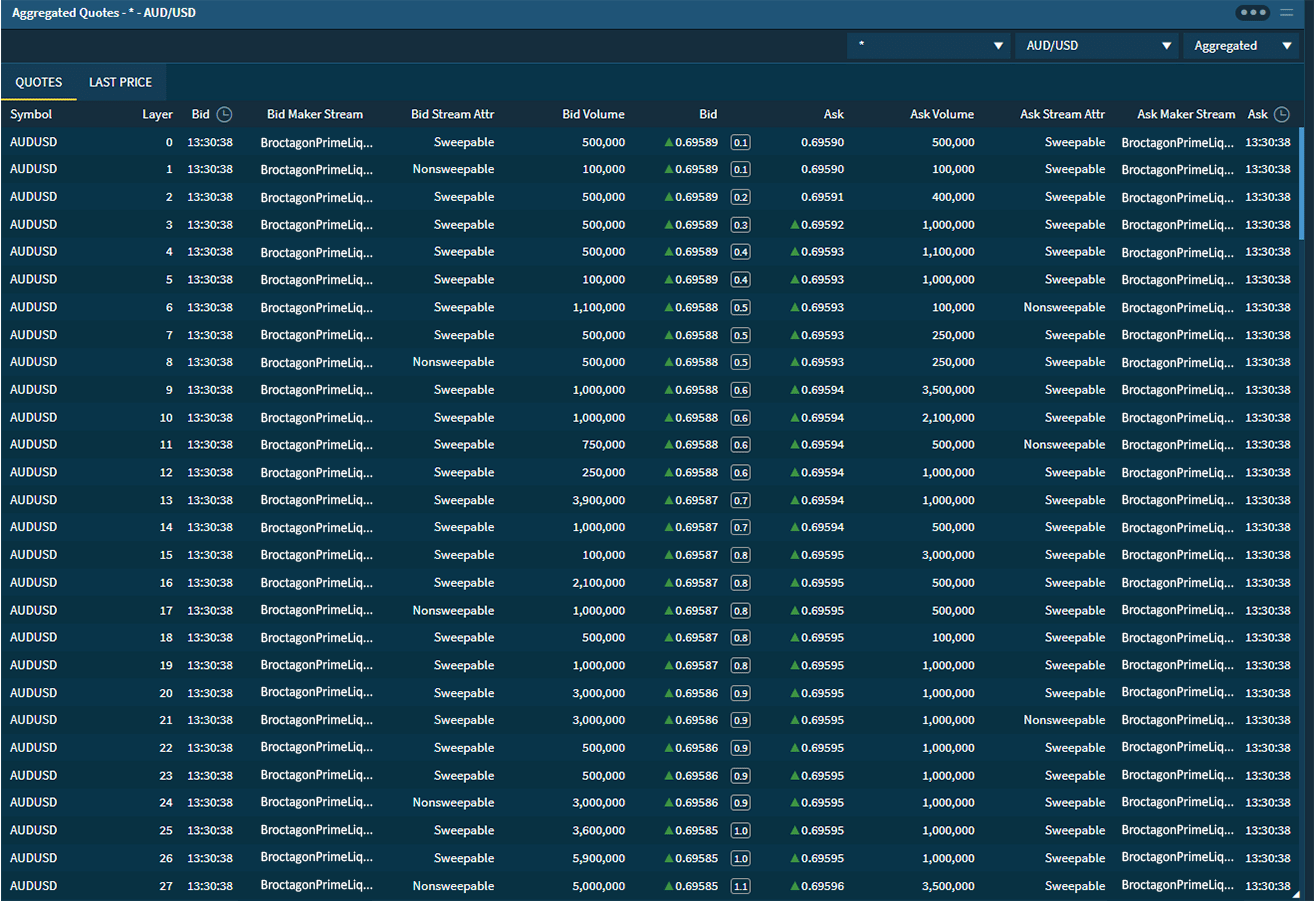
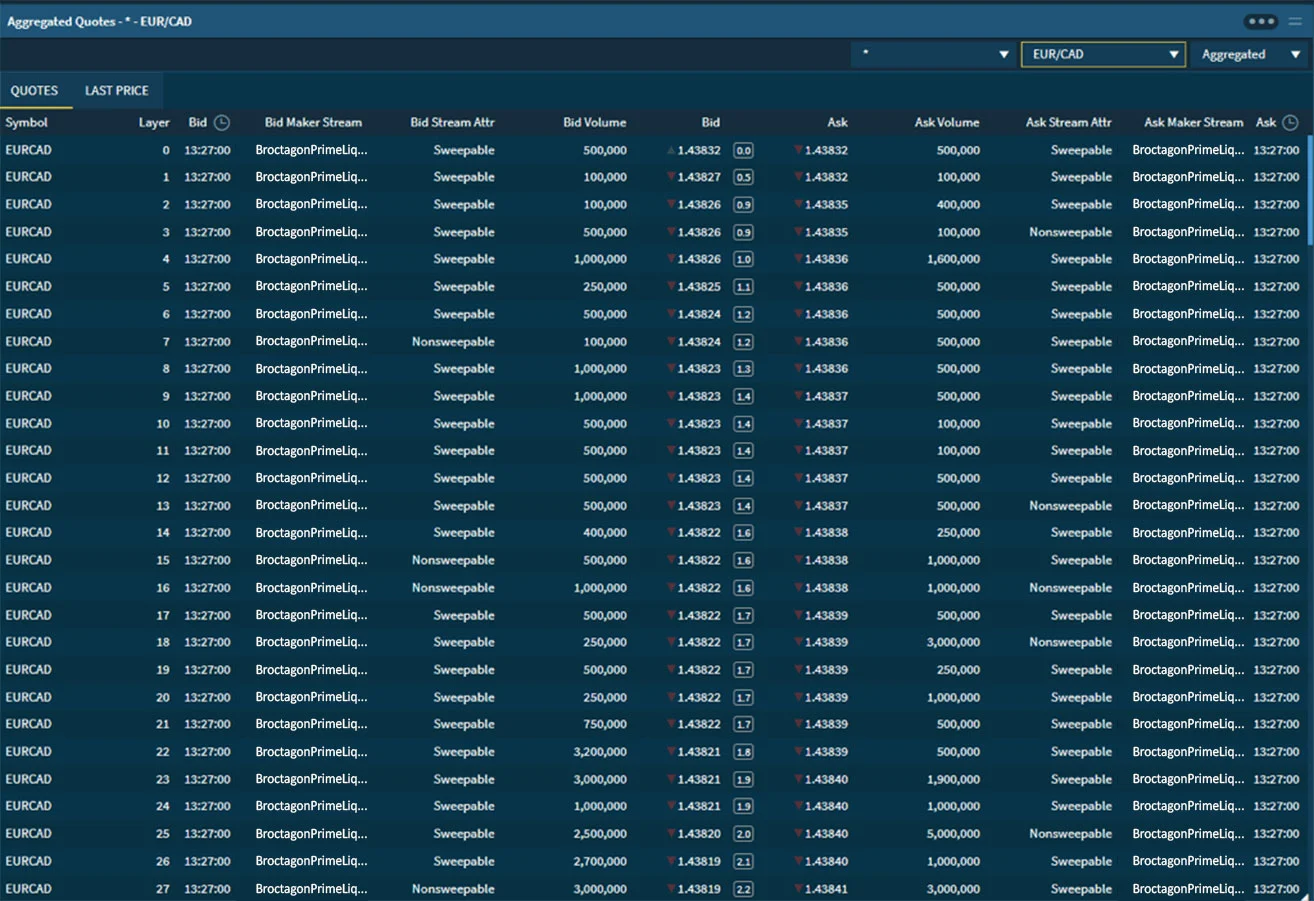
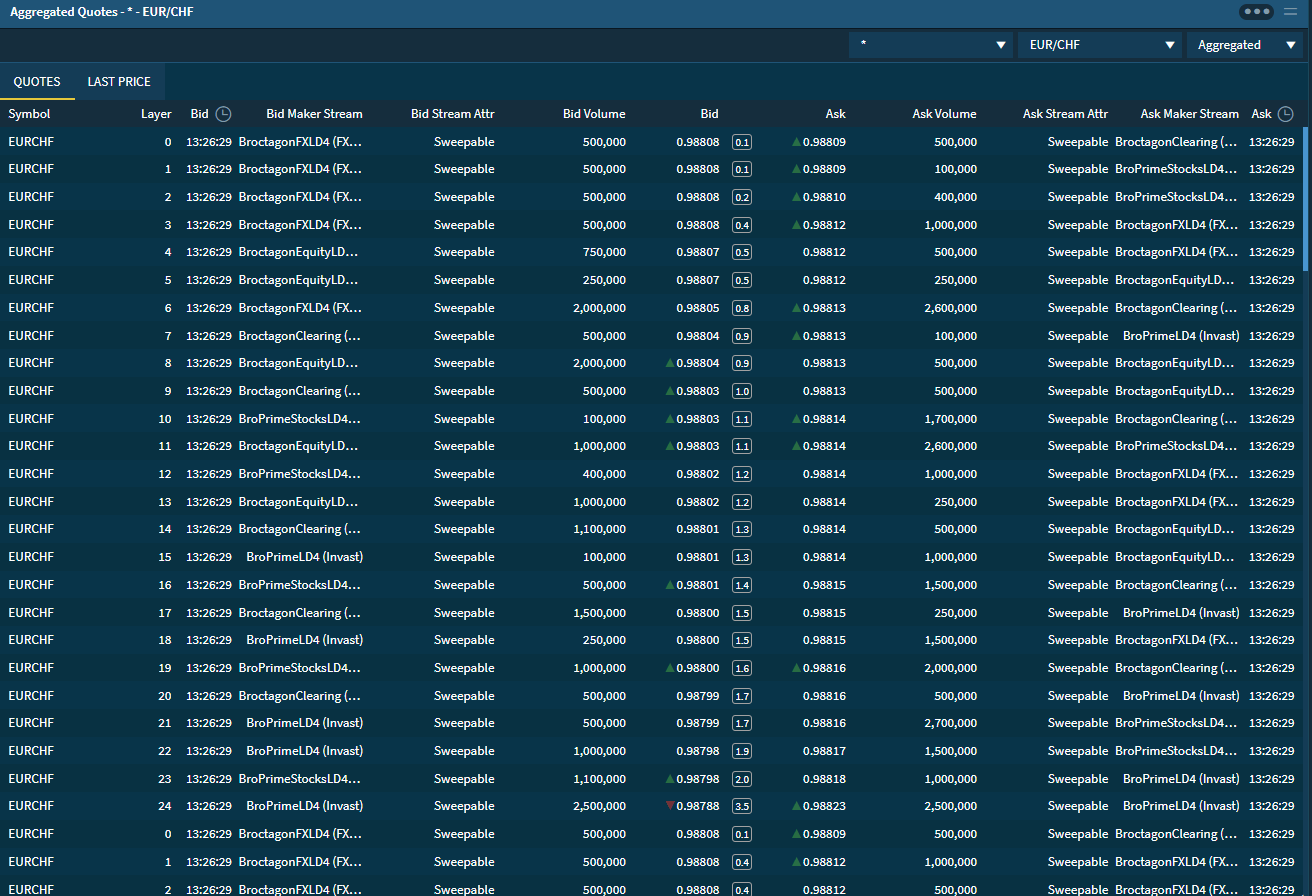
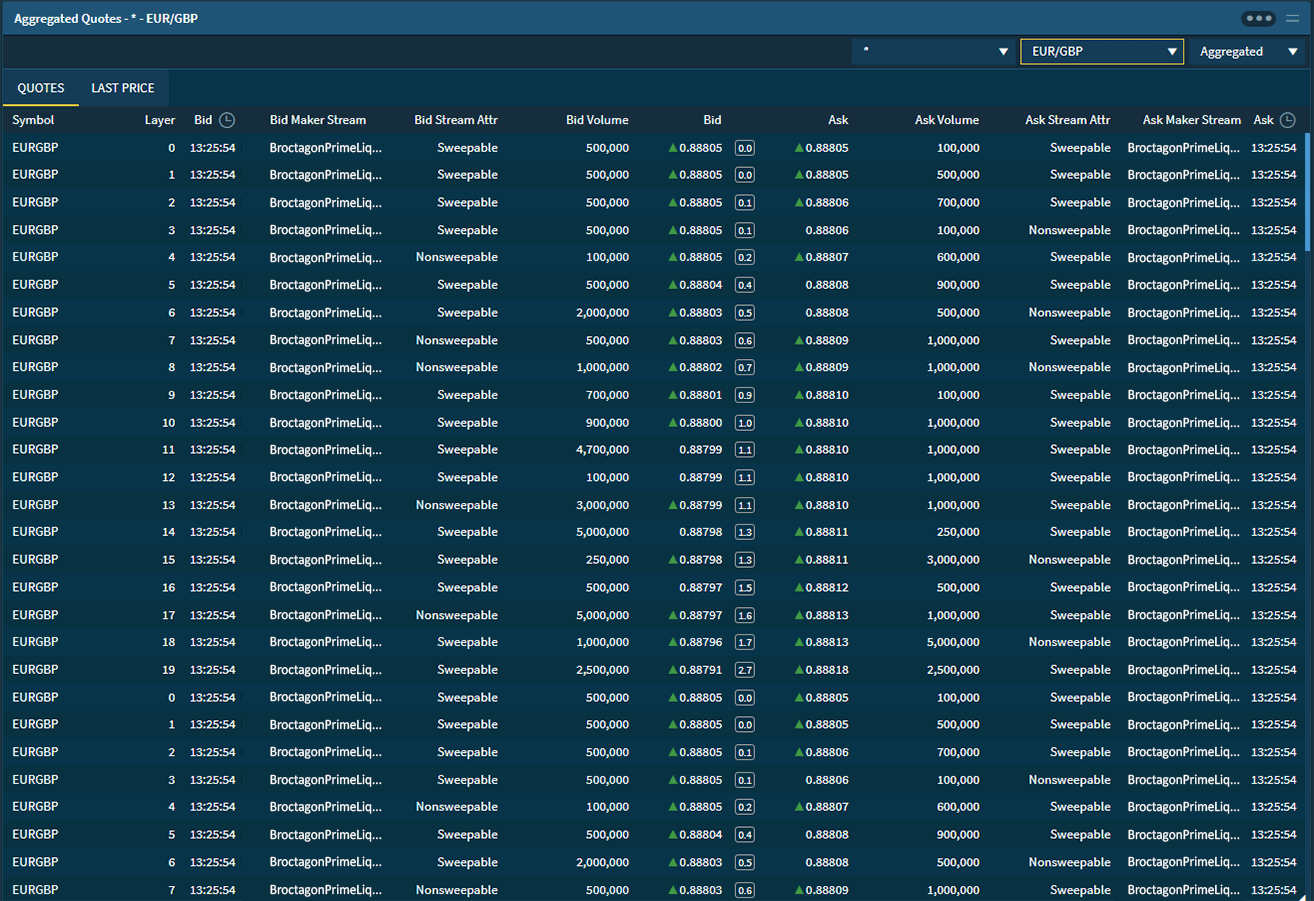
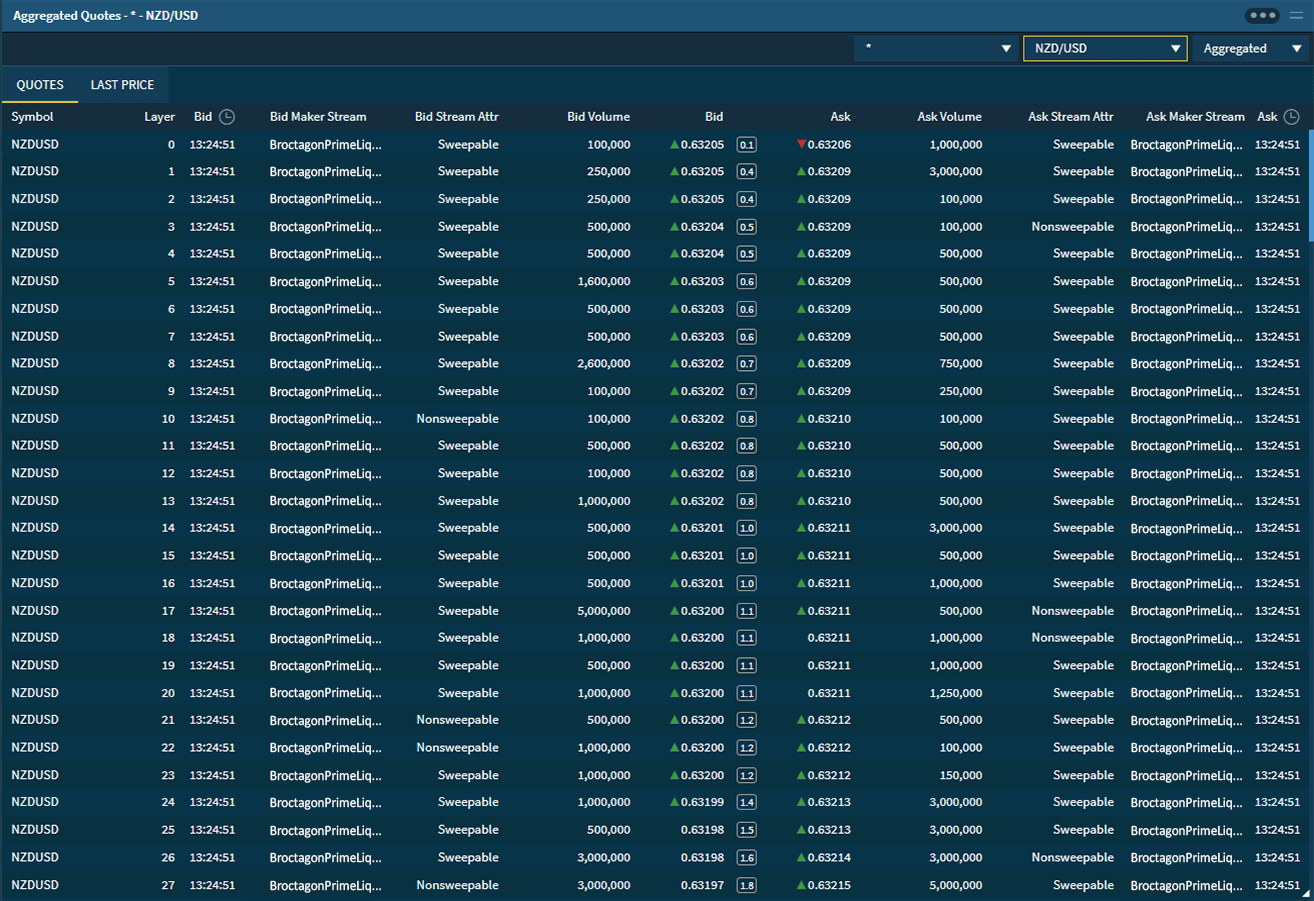
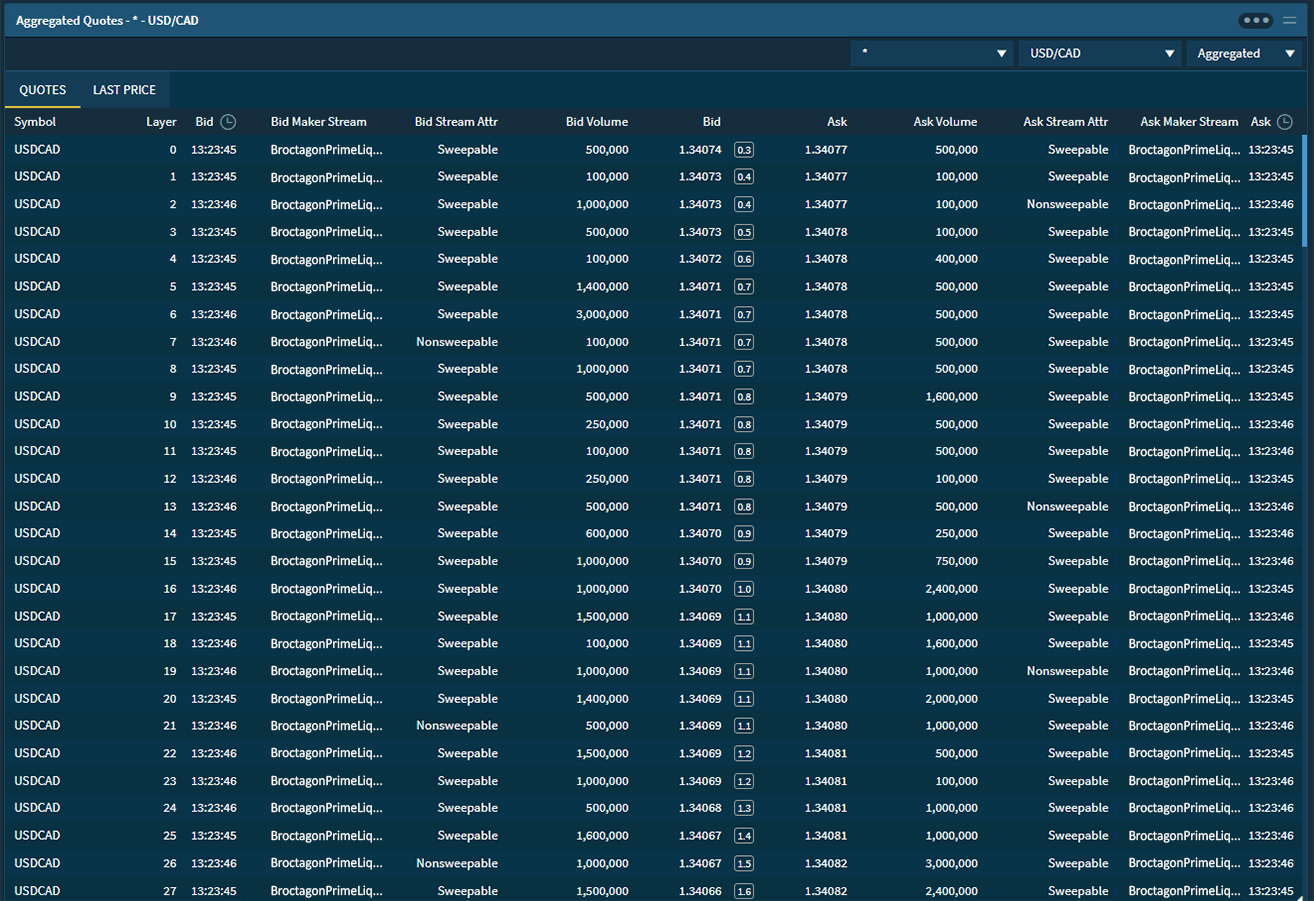
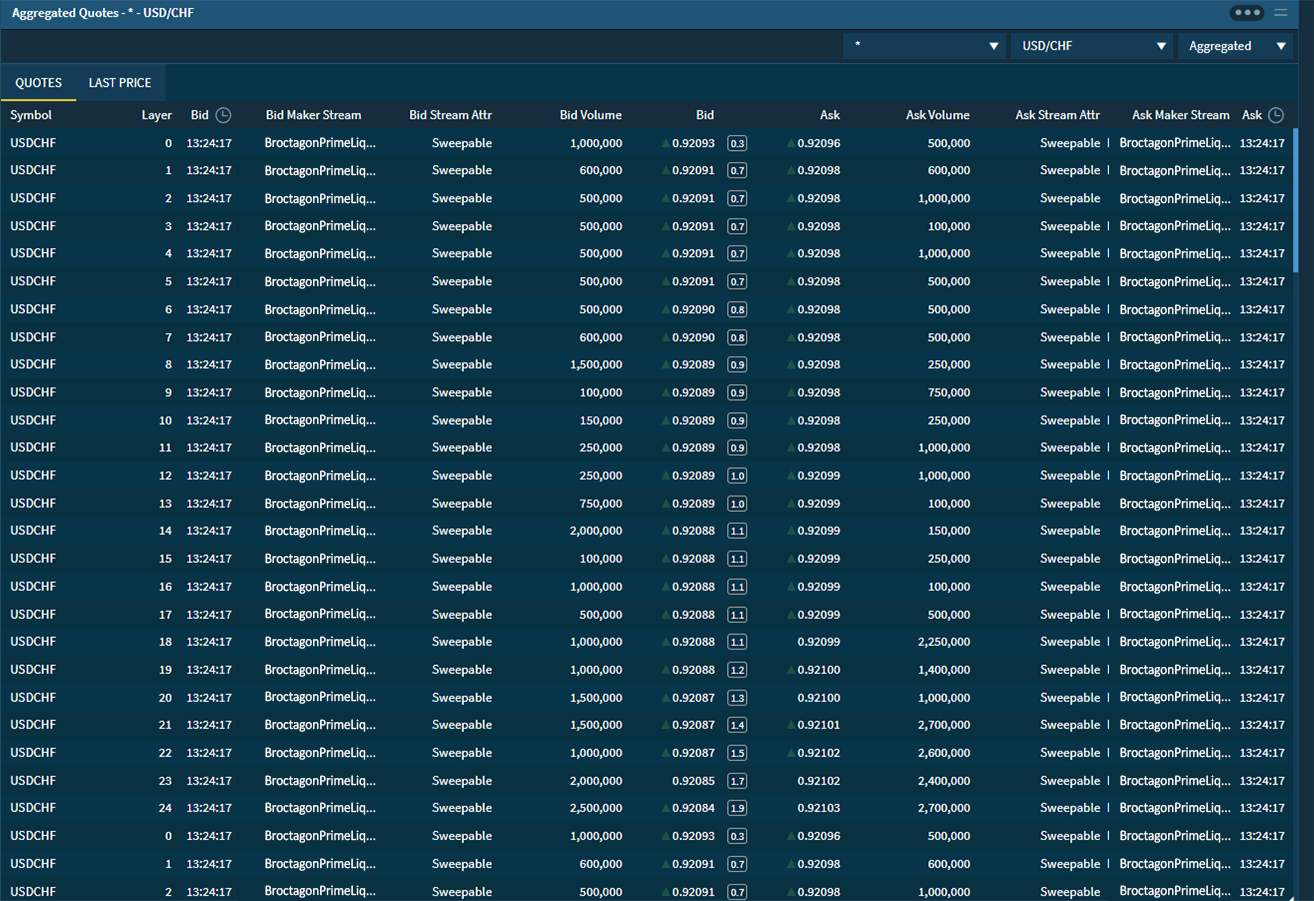
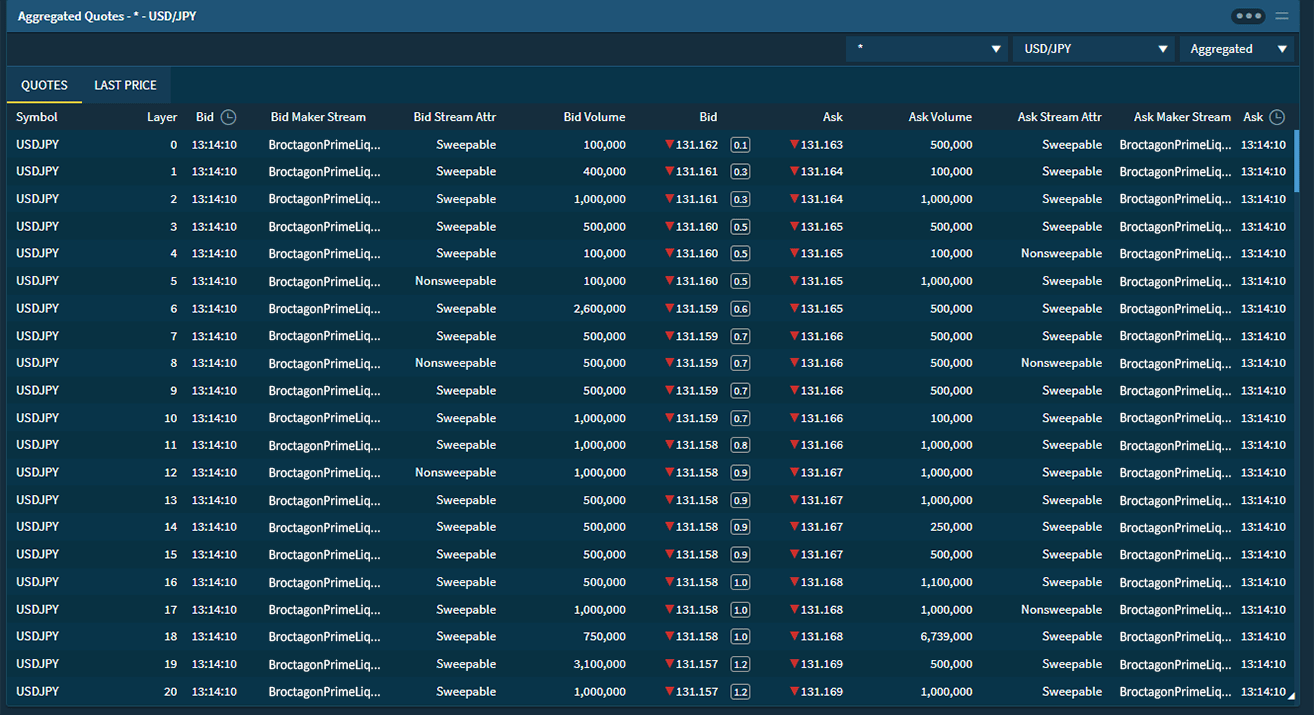
Information and data have become the highest priority targets in digital business around the world. Broctagon offers high availability solutions for protection against attacks that put client information at risk of theft, minimize operational disruption while delivering ultra-low latency to all trading environments.
Threat
Monitoring
Continuous security monitoring of private cloud and physical data centre environments
Server
Protection
Disaster
Recovery
Routine disaster tests to verify projected recovery timings and data integrity
Multiple Server Nodes
Maintaining of business operations during cyber attacks with minimal disruption
System Penetration Testing
One cyber incident is enough to cripple any business with extensive loss to income, reputation and clientele.
Ensure Your Digital Assets Are Well-Protected
In the current digital era, cyber protection must be robust enough to tackle the ever growing threats to system security. To give security systems and personnel real scenarios in dealing with an intrusion, Broctagon’s team of OSCP testers performs a comprehensive ethical hacking procedure to validate and scan for vulnerabilities in digital security in accordance with the OWASP-based best practices for penetration testing framework.

How Does it Work?
The system penetration testing is suitable for companies that have already taken security measures, and now want to verify the efficiency of these measures. Namely, the penetration testing is not a complete security audit, but is rather aimed at discovering the security deficiencies that enable the attacker to reach their goals as simply as possible.
Establishing Test Parameters
We define beforehand the parameters and goals for penetration testing – Types of attack to simulate, the attacker’s motivation, internal or external origin of attack, and more.
Executing Ethical Hack Procedures
We perform a controlled attack on infrastructure such as web devices, servers, users’ computers. No harm done to infrastructure throughout the hacking process.
Generating Test Report
During the test, all deficiencies are recorded and then presented in the final report. We provide information on the softest points of the system along with recommendations for the abolishment of deficiencies.